Reverse Proxy Server: Introduction
|
Reverse Proxy Servers: Introduction | Basics | mod proxy html | IIS back-end server |
| Uniform Server 3.5-Apollo Reverse Proxy. |
If you have searched the Wiki you will have wondered why so many mini-servers! These were designed to explore various aspects and architectures using multiple servers without the tedium of setting each server up from scratch. The following looks at reverse proxy servers.
Reverse proxy
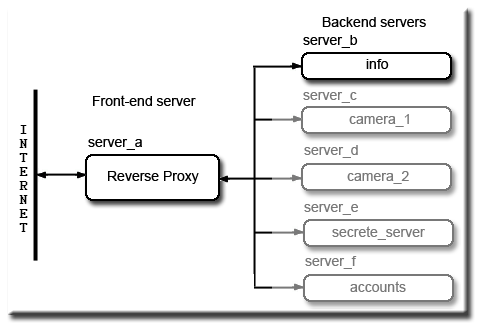
A reverse proxy is all about hiding a bank of servers behind a main server. There are several reasons why you want to do this, for instance to reduce the load on your main server by allowing other servers to take the strain. These would be dedicated boxes running specific specialised tasks requiring raw computing power either to create web pages or to access and process data from databases before being served to an end user.
Other users may want to integrate various media from smaller servers such as web cameras or even part of an intranet. All these servers are hidden and not directly accessible from the Internet. It is the responsibility of the main server (reverse proxy) to grant and allow access from the Internet.
The advantage of this set-up, only one domain name required, password access if used is centralised. Hidden servers are all mapped into the main server's name space (fred.com) making them transparent to an end user.
|
http://fred.com/ |
Mapping is not complex its as easy as creating folders, assign each server a folder name, for example Suppose your domain name is fred.com a user would access the above by typing the URL's shown on the left into their browser address bar: |
|
The real significance a user sees only a set of seamless folders for your domain. Your main server can still be used to server web pages the other servers are there to either reduce your main server load or to enhance content that is not possible any other way.
|
Front-end Server
For this tutorial you can use either Uniform Server 3.5-Apollo or mini-server 20 for the front-end server. They both require the same proxy files (modules), mini-server 20 comes complete with matching modules these cannot be used with Apollo if you decide to use Uniform server as a proxy server follow the instruction below to obtain the correct versions.
Uniform Server 3.5-Apollo Proxy Files
The required files for running a proxy server are not included with Uniform Server 3.5 no big deal. Go to Apache archive download site and download file apache_2.0.59-win32-x86-openssl-0.9.7j.msi to extract the binaries follow the instructions on this page Support and download.
mod_proxy.so mod_proxy_http.so mod_proxy_ftp.so mod_proxy_connect.so |
Copy these four files to folder: \Uniform Server\udrive\usr\local\apache2\modules |
Edit Apache's configuration file: httpd.conf
Located in folder: \Uniform Server\udrive\usr\local\apache2\conf
Locate these lines:
LoadModule proxy_module modules/mod_proxy.so LoadModule proxy_connect_module modules/mod_proxy_connect.so LoadModule proxy_http_module modules/mod_proxy_http.so LoadModule proxy_ftp_module modules/mod_proxy_ftp.so |
Un-comment as shown. (remove the hash #) |
Restart server for the settings to take place.
That completes the set-up you can now use proxy commands in your configuration file this I cover this later.
mini_server_20_reverse_proxy
This tutorial assumes you are using mini-server 20 download from this page advantage of this the server is preconfigured and includes several configuration files you can swap in while following each example.
Start the server; your browser will automatically start if not already running. The main index page displays four links, info, Wiki, Wordpress and Joomla. Click either link the expected result will be page not found, this server although fully functional has not been set-up to proxy any back-end servers. This will be addressed in the tutorial.
Back-end Server Web Sites
In this tutorial I want our back-end server (server_b) to serve all web pages. Being lazy I will be using mini-server 6 check this page for details.
Run server 6 and type http://localhost:8086/ into your browser. An index page is displayed check out test sites test1; test2 and test3 ignore their content. What won’t be immediately apparent sites test1 and test 2 use relative links while site test3 uses web root relative links? You will see the significance of this latter.
Sites are accessible by typing the following into a browser:
- http://localhost:8086/ -- Main index page
- http://localhost:8086/test1/ -- Uses relative links
- http://localhost:8086/test2/ -- Uses relative links
- http://localhost:8086/test3/ -- Uses web root relative links
Both servers are now ready to run the tutorial examples.
Security
Before I continue lets have a quick look at security issues. Although we are experimenting and well! Basically having a play it’s important to restrict access to the servers.
The only server allowed accessed from the Internet is our front-end server. The default installation of Uniform Server is to deny access. You can open the server to allow access especially if you want to perform real tests say using a DynDNS account or even your real domain.
Front-end Server
Open the file .htaccess in folder \udrive\www and set the following three lines to suit your needs:
|
|
|
When running a reverse proxy on-line it must be prevented from being an open proxy otherwise any Internet user can use it for forwarding and covertly access the Internet through your server. OK sounds dramatic! The solution is to switch proxy requests off this prevents all external proxy requests being processed however internal ones are still honored.
Feeling paranoid! Well you can further restrict access by targeting a specific machine using a proxy block. Putting these two together gives the following block of code always add it before using a reverse proxy:
|
ProxyRequests off: Prevents any external requests through the proxy engine. Optional Proxy block: Not really required shown as an example it restricts local access only. |
Most important is Proxy Requests Off
Note: When you put your servers on-line either remove the proxy block <Proxy *></Proxy> or replace the IP address with a list of IP addresses you wish to allow.
Back-end Servers
Each back-end server requires an .htaccess file to restrict access as follows:
|
If your back-end servers reside on a different machine change the “Allow from 127.0.0.1” to the IP address of the machine that is running the proxy server.
I cannot think of one reason why you would want to open any back-end servers so don’t, always restrict access.
Summary
That completes the front and back-end server overview including security. Enabling the front-end server, as a proxy is straightforward un-comment the appropriate lines in Apache’s configuration file.
Both front and back-end server are ready to run its time to look at some practical proxy examples starting with a basic configuration.
| Ric |