Firewall: Router
|
Firewall: Home | Windows XP | ZoneAlarm | Router | TCP View |
|
Firewalls |
Broadband with its inherent speed allows many users to share a single Internet connection. Wireless routers have become a common feature in many homes these networking devices are installed between your cable or DSL modem and your computers. All include some form of firewall protection filtering data that enters your network from the Internet.
|
There are many different brands of routers however most of them function in a similar way. The firewall on these devices is configured using a web browser to navigate to the router’s built-in IP address. These routers contain several pages allowing you to configure different aspects of the router. What's important the firewall in these devices is known as a hardware firewall, it does not conflict with a software firewall on your PC. A routers firewall guards the entrance to a network hence protects all PCs connected. To harness the full power of these firewalls additional steps are required during configuration. |
Unlike software firewalls, hardware firewalls are always active as long as the router itself remains switched on. Before making changes to a basic configuration ensure your network is working correctly refer to your routers documentation for details.
Hardware firewalls offer some additional possibilities and complexities that I cover.
Security
This is a tricky subject, as there are a wide variety of possible settings, and not every home router will have certain options. What I will do is give you a list of potential settings and what they can do to enhance your firewalls security. Compare these to your routers documentation to ensure that you maximize security.
Block ICMP traffic, 'stealth' mode: ICMP is the protocol used most commonly by the PING program. This program queries a given IP address and reports back if a computer answers. It forms the basis for the myriad of 'scanner' programs freely available on the Internet. These scan a range of IP addresses looking for computers that respond. On receiving an answer back to the ICMP request are then targeted by the scanner for further, more intrusive measures to discover security weaknesses. If your firewall blocks ICMP traffic, your system is effectively invisible to casual Internet snoopers
Stateful packet inspection: A firewall method that takes a deeper look at each data packet received, instead of just approving or dropping them based on the set rules of the firewall (allow x data from y computer on z port). This type of firewall will compare a data packet to others received previously, and will also examine the full contents of the data. This enables it to prevent attacks that traditional firewalls would not catch, such as a DoS (Denial of Service) attack made up of massive amounts of identical data packets intended to overwhelm the target system.
Disable remote administration: Home routers have a facility to allow configuration over the Internet you are required to enter a user name and password. To increase security disable this feature use a physical connection to configure your router.
Attack detection: Many home routers are equipped to specifically identify and log certain common types of attack for example denial of service attacks and other well known exploits. These are generally enabled by default check your routers documentation.
Disable file and printer sharing: Home routers have printer and file sharing enabled by default. Check your routers documentation and disable it. With it enabled allows remote users to access shared files and devices on your system.
Allowing applications through a router
Configuring a home router to allow applications to work correctly requires a different process for each brand and type. These procedures are similar for most wireless home routers.
To share an Internet connection most home routers use NAT (Network Address Translation) these function by storing Internet data requests from computers inside the home network in a table. Data received from the Internet is compared to the request stored in this table to see if the source and data type matches. If it does, the data from the Internet is forwarded to the computer in the network that requested it. If not, it is dropped.
The trouble is that NAT only recognizes certain common data types and will not pass on data that is not recognized. This leaves many file transfer and voice/video conferencing programs being potentially dropped. To resolve this issue you will find special application pages within the set-up that target these programs again read the documentation to see what needs to be set.
Hosting websites - Port forward
Hosting a website is different to using an application, when you are hosting, it's implied data traffic is coming from the Internet to your computer or network, not the other way around. This is a problem, because by default, firewalls drop all unsolicited traffic from outside the network, if you have a website, no one's going to see it without some changes.
Home routers that use NAT (Network Address Translation) means you cannot simply open up ports in the firewall to allow hosting of websites.
Instead, you need to create a virtual server (commonly referred to as port forwarding) for each service you wish to make available over the Internet.
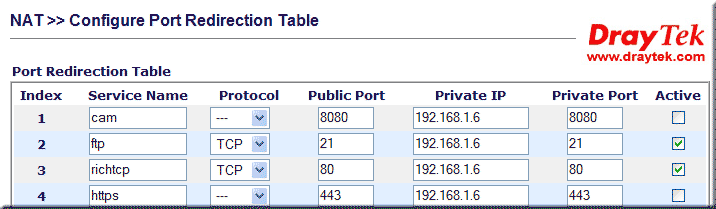
A virtual server is a set of instructions given to the home router, telling it that if data comes in over a specific port (say TCP port 80 for hosting a website) that data should be allowed through the firewall and forwarded to a specific computer inside the network. In this way, you can make your website available without compromising your firewall security.
Creating a virtual server (port forwarding) tends to be the same for most home routers. To implement first check your routers documentation if you have problems check out this excellent site PortForward it is dedicated to this topic.
| Example of creating a virtual server for hosting a website (TCP port 80). |
|---|
|
After you save this information, all data coming from the Internet to the firewall on TCP port 80 will be redirected to your hosting computer, thus allowing access to your website.
Logging
Most firewalls will automatically keep logs of all dropped traffic. Some will also keep track of all successful (accepted) connections. This data is kept in a log file created by the firewall software
All home routers have a log viewing option, one thing common to all logs is that they will reveal the source (IP address) of incoming data, as well as the port it was intended for. This can be useful information, especially if your system has been compromised.
Where to next
This section is only intended to get you up a running more importantly provides a clue what to search for on the Internet.
| Ric |