Reverse Proxy Server 2: Introduction
|
Reverse Proxy Server: Introduction | Basics | mod proxy html | mod proxy html 2 | SVN 1 | SVN 2 | SVN 3 | SVN 4 | Wiki | Deployment | IIS back-end server
|
|
| Uniform Server 5.0-Nano Reverse Proxy. |
Uniform Server 5.0-Nano is ideal for creating front and back end servers. Depending on number of back-end servers it is possible to test a complete architecture on a single PC. This allows you to preform tests before deploying on dedicated PC’s.
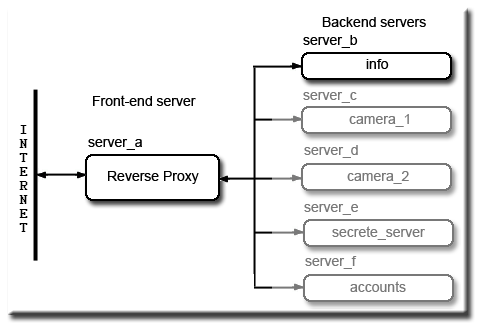
This tutorial revisits building a reverse proxy server. It covers basic concepts and demonstrates some of UniServer 5.0-Nano’s unique features making the whole process very easy.
Reverse proxy
A reverse proxy is all about hiding a bank of servers behind a main server. There are several reasons why you want to do this, for instance to reduce the load on your main server by allowing other servers to take the strain. These would be dedicated boxes running specific specialised tasks requiring raw computing power either to create web pages or to access and process data from databases before being served to an end user.
Other users may want to integrate various media from smaller servers such as web cameras or even part of an intranet. All these servers are hidden and not directly accessible from the Internet. It is the responsibility of the main server (reverse proxy) to grant and allow access from the Internet.
The advantage of this set-up, only a single domain name is required, password access if used is centralised. Hidden servers are all mapped into the main server's name space for example fred.com making them transparent to an end user.
|
http://fred.com/ |
|
Front-end Server
For this tutorial we need a front-end server (server_a), create a new folder for example c:\server_a extract UniServer 5.0-Nano to this.
Our front-end server requires configuring to run as a proxy server.
Enable Proxy Modules
Edit Apache's configuration file: C:\server_a\UniServer\usr\local\apache2\conf
Locate these lines:
#LoadModule proxy_module modules/mod_proxy.so #LoadModule proxy_ajp_module modules/mod_proxy_ajp.so #LoadModule proxy_balancer_module modules/mod_proxy_balancer.so #LoadModule proxy_connect_module modules/mod_proxy_connect.so #LoadModule proxy_ftp_module modules/mod_proxy_ftp.so #LoadModule proxy_http_module modules/mod_proxy_http.so |
Un-comment as shown. (remove the hash #)
LoadModule proxy_module modules/mod_proxy.so #LoadModule proxy_ajp_module modules/mod_proxy_ajp.so #LoadModule proxy_balancer_module modules/mod_proxy_balancer.so LoadModule proxy_connect_module modules/mod_proxy_connect.so LoadModule proxy_ftp_module modules/mod_proxy_ftp.so LoadModule proxy_http_module modules/mod_proxy_http.so |
That completes the set-up you can now use proxy commands in your configuration file this I cover this later.
Note: We are not using two of the modules hence they remain commented.
Back-end Server
We also require a back-end server (server_b). Create a new folder c:\server_b extract UniServer 5.0-Nano to this.
Move Servers
One of Uniform Server’s unique features is the capability to run more than one complete server on the same PC. You will have noticed UniTray’s icon displays one (meaning standard ports). Moving UniServer increments this digit and so on for each server move. In reality it’s not just a port change but a complete server update, running server status displays the server characteristics.
Move Servers:
- Stop all running Uniform Servers
- Start UniTray, in folder C:\server_b\UniServer double click on Start.exe tray icon created.
- Move servers, Left click tray icon > Advanced > click Move Servers multi-server operation.
- In the pop-up window at all prompts press enter to accept defaults.
- The tray icon will display 2, if you already use a server with this number repeat steps 3 and 4 each server must have a unique number.
- I run a Wiki on 2 hence repeated the above.
- Before proceeding you need to use the new server ports.
- To find these: Left click tray icon > Server Status
I moved the servers to icon 3 hence Apache port = 82 and MySQL port = 3308
Both servers are now ready to run tutorial examples.
Security
Before I continue lets have a quick look at security issues. Although we are experimenting and well! Basically having a play it’s important to restrict access to the servers.
The only server allowed accessed from the Internet is our front-end server. The default installation of Uniform Server is to deny access. You can open the server to allow access especially if you want to perform real tests say using a DynDNS account or even your real domain.
Front-end Server
Open the file .htaccess in folder C:\server_a\UniServer\www and set the following three lines to suit your requirements:
|
|
|
When running a reverse proxy on-line it must be prevented from being an open proxy otherwise any Internet user can use it for forwarding and covertly access the Internet through your server. OK sounds dramatic! The solution is to switch proxy requests off this prevents all external proxy requests being processed however internal ones are still honored.
Feeling paranoid! Well you can further restrict access by targeting a specific machine using a proxy block. Putting these two together gives the following block of code always add it before using a reverse proxy:
|
ProxyRequests off: Prevents any external requests through the proxy engine. Optional Proxy block: Not really required shown as an example it restricts local access only. Place the code inside the first Vhost see next page |
Most important is Proxy Requests Off
Note: When you put your servers on-line either remove the proxy block <Proxy *></Proxy> or replace the IP address with a list of IP addresses you wish to allow.
Back-end Servers
Each back-end server requires an .htaccess file to restrict access as follows:
|
If your back-end servers reside on a different machines add another line “Allow from ***.***.***.***” use the IP address of the proxy machine. I cannot think of one reason why you would want to open any back-end servers so don’t, always restrict access. |
Summary
That completes front and back-end server overview including security. Enabling the front-end server to run as a proxy is straightforward un-comment appropriate lines in Apache’s configuration file.
Both front and back-end server are ready to run its time to look at some practical proxy examples starting with a basic configuration.