MySQL Security: Difference between revisions
(Punctuation and grammatical changes; some clarification.) |
m (Reverted edits by Upazixorys (Talk); changed back to last version by BobS) |
| (One intermediate revision by one other user not shown) | |
(No difference)
| |
Latest revision as of 08:32, 24 November 2010
| MySQL Security |
Introduction
After extracting Uniform Server, your first task should be to change the MySQL password. However doing so will render all pre-configured plugin applications inoperable.
To resolve this issue, you can edit each applications configuration file and change the password accordingly. This method is very high risk especially if you intend to run a production server.
The following is a step-by-step guide how to secure MySQL server on Uniform Server.
Security issues
You probably are wondering what all the fuss is about. The following attempts to explain the levels of security and why the root user is so dangerous.
Root User
A default installation of Uniform Server has a single MySQL user named root with password root. This user has full global privileges. The significance of this privilege is server wide, meaning the root user has full power to create and delete any database or table.
Changing the MySQL password (root user password) from Apanel protects this user. However the root user should only be used for server administration and be the only user to connect to the server with these privileges.
Application connection
When installing an application, you are required to enter a database name along with a user name and password. Using the root user for installation is convenient and generally installation will proceed with no problems.
Although convenient (unless steps are taken), using root is an extremely serious security issue. Every time an application connects to the MySQL server it does so with all granted privileges. Should the application be compromised in any way, your entire MySQL sever is at risk.
Application security
Application programmers do their utmost to protect the application from malicious users. If the application becomes compromised, generally only the application is killed. However if the application connected with full privileges (as root) you can kiss your MySQL server good-bye.
To put the above into context for a test server, the only person that can compromise your server is you, which is not an issue. On the other hand, when putting your servers online, any user can potentially compromise your servers, so you must take security seriously.
General Steps
- Change the MySQL root password
- Install an application using root user
- Create a new user with limited privileges for that application's database only
- Change the application's configuration file to connect using the above user.
Detail
Change MySQL password
|
Change MySQL password
|
Install an application
- Install application as per instructions.
Note: From the above MySQL server host is localhost user name root password fred123
Use the password you configured. - For the remainder of this example, I will assume you are using the MediaWiki plugin V55_MediaWiki_1_15_1.exe
Note: This is pre-configured and uses user name root and password root
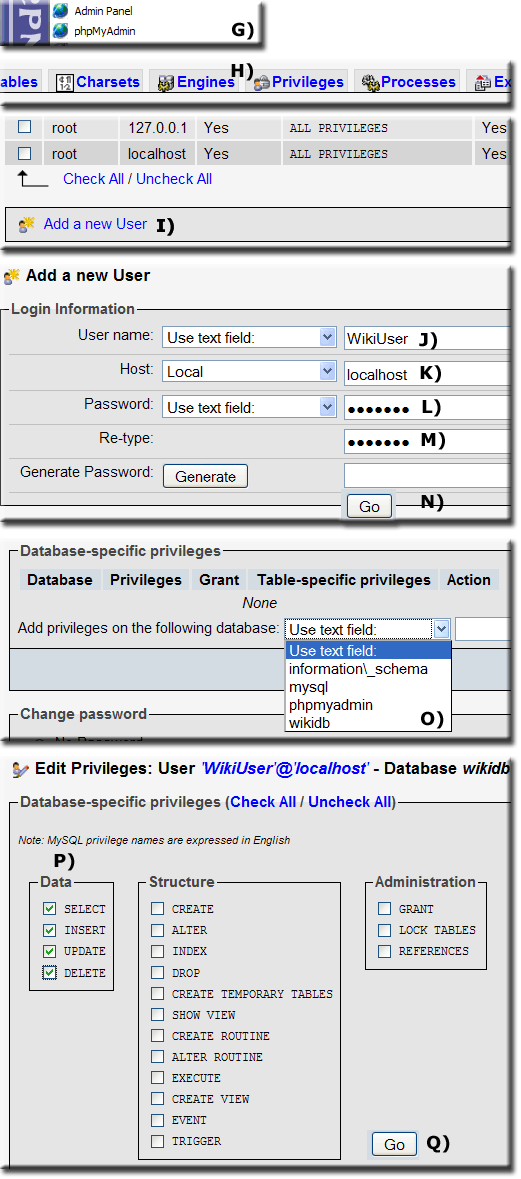
Create a new user
|
Change MySQL password
Note: A user in this context is the name of a MySQL user that is allowed to connect to the MySQL server. This name has no relationship to any application's users.
|
Edit application configuration file
Continuing with our MediaWiki example final step is to edit the configuration file.
Open file UniServer\www\wiki\LocalSettings.php in a text editor.
|
|
General note
After making any significant changes always restart servers and flush your browser cache and delete all cookies.
For Firefox:
- Tools > Options > Click Privacy > Click Show cookies button > Click Remove all cookies
- Tools > Options > Click Advanced > Click Clear Now
Conclusion
Installing applications using root makes the whole process relatively easy since you have full privileges. After installation check the application runs, then secure the MySQL server with a user that has restricted privileges as explained above.
For a production server it is essential to secure your MySQL server. For a test server the choice is yours, however if you put a test server online you must secure it.