Stunnel: SSL Certificate: Difference between revisions
(New page: <span id="top"></span> <div style="padding:0;margin:0; border-bottom:3px inset #000000"> {| | MPG UniCenter || Stunnel: Home | [[Stunne...) |
(No difference)
|
Revision as of 19:41, 4 June 2008
|
Stunnel: Home | Upgrade 4.24 | Install | SSL Certificate | Single Vhost | Resolved | Basics | Cost | Original |
|
Stunnel SSL Certificate and Key generation |
Before going live with your secure server it is imperative you generate a new certificate and public key for Stunnel. The process is extremely easy, first shut down both servers and follow the instructions below.
Generating a certificate
The batch files mpg_create.bat allows you to create the private key and public key (certificate) in one go.
The file is located in folder: *\Uniform Server\udrive\home\admin\www\plugins\stunnel_424\bin
- If running shut down your servers.
- To start the process double click on the batch file mpg_create.bat.
- First the private key is automatically created and requires no input from you.
- The next phase is a Certificate Signing Request (CSR).
During this generation process you will be prompted for several pieces of information. These are the X.509 attributes of the certificate. - I have highlighted in bold the type of information you enter.
|
Country Name (2 letter code) [PL]:UK |
You can repeat this process at any time, have a play and get a feel for what’s going on. The information you enter is unimportant with the exception of FQDN (fully qualified domain name) if you have one use it (its the full address you would enter in a browser apart from the http:// bit).
Note 1: A default value is displayed in square brackets press return to accept this value. If you are feeling lazy press return at each prompt. The resulting certificate is fully functional however it does not look very professional when displayed in a browser.
Note 2: The only thing of importance each certificate you generate is unique.
It really is that easy to produce a self signed certificate to secure your personal server. If you want some background information take a look at this page SSL basics.
Ports
Port 80
This is the standard port for unsecured web page servers, Uniform Server (Apache) defaults to this. If you have changed this default setting you need to change Stunnel’s configuration file to match your new port.
Port 443
This is the standard port for secure web page servers and Stunnel’s default setting. If you need to use a different port change Stunnel’s configuration file as required.
Internet access
When you put your servers (Apache and Stunnel) online you must have ports 80 and 443 open for public access otherwise your servers will be inaccessible. Make sure your firewall does not block these ports. In addition if you are using a wireless router (or other router) remember to forward both ports 80 and 443.
Note: If you have changed the ports use these values instead.
Help
I have purposely avoided showing how to set the ports on your firewall or router. The reason being each firewall and router use different methods; however do not be discouraged there is a complete site dedicated to this " portforward.com.
I your firewall or router is not listed on this site then it does not exist, yes it’s that comprehensive. Start from this guides page.
Not sure – Port bashing
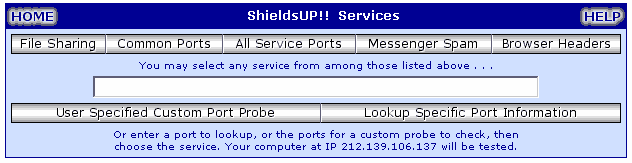
You have opened your server ports or have you? Now would be a good time to check that you were successful. This next site is a must visit Gibson Research its where you can get a free bashing or more acutely port probing.
Towards the end of this page click the link ShieldsUP, at the bottom of this new page click precede which takes you to the main ShieldsUP page. (You need to follow the links in the above that’s the way it works). Once you have navigated to the page you will find this control panel:
To perform a full port scan (probe) click the All Service Ports link. When the test completes you will see two red squares one for each port (80 and 443) indicating your servers are accessible. Do not be alarmed by the fail message you opened these ports however if you see any other ports open its probably wise to check these out.
Fully secure server
Your web site is public on both the secure (port 443) and insecure (port 80) ports. This means users can access your pages using either a secured or unsecured connection. You may only want access via the secure port, to achieve this either block incoming port 80 in your firewall or disable port forwarding for port 80 in you router.
Confirm you have correctly disabled port 80 by repeating the port probe at Gibson Research.
Conclusion
I have shown how easy it is to use Stunnel for a personal secure server. If you need more detail check out the additional pages Resolved, Stunnel Basics and Stunnel Original write-up these I separated out for clarity.
Perhaps you do not wish to secure your entire server but only a single virtual host. I have had several requests how to-do this which I cover on the next page Securing a Single Vhost.
| Ric |